The good news is that more and more businesses, schools and government agencies are switching to a hosted VoIP phone system, so they can take advantage of key benefits like:
- Dramatic up-front and ongoing cost savings
- Seamless scalability in both directions
- Total mobility
- Advanced calling features
- Unified communications
- Business continuity
- Integration with other systems in the environment (e.g. CRM, billing, etc.)
However, the bad news is that the popularity of VoIP phone systems has attracted the attention of hackers who are trying to steal private data and commit identity theft. Here are four major types of VoIP fraud:
Call Transfer Fraud
Call transfer fraud happens when hackers break into a VoIP PBX (private branch exchange), in order to make free long distance calls and/or provide their own subscribers with free long distance calls.
Traffic Pumping Fraud
 Traffic pumping fraud happens when hackers break into a VoIP network and generate unauthorized calls to a premium number. The victim ends up with a large bill, and the hacker gets a share of the revenue. Often, this type of VoIP fraud takes place on weekends and holidays when victims are not using and monitoring their system. For example, on the recent July 4th holiday weekend, there was a spike in attempted telecom fraud attacks.
Traffic pumping fraud happens when hackers break into a VoIP network and generate unauthorized calls to a premium number. The victim ends up with a large bill, and the hacker gets a share of the revenue. Often, this type of VoIP fraud takes place on weekends and holidays when victims are not using and monitoring their system. For example, on the recent July 4th holiday weekend, there was a spike in attempted telecom fraud attacks.
Fake Answer Supervision
Fake answer supervision happens when hackers modify the answer signal of a call, in order to bill for calls that do take place (and which should therefore not incur billing). There are a few main types of fake answer supervision, all of which are designed to increase the length of a call and therefore the cost:
- Calls are routed to a recorded message that plays a ringing tone, followed by a recording.
- The carrier returns the answer signal when the ringing begins, instead of when the customer actually answers.
- Calls are not terminated when recipients hang up, but when callers disconnect. Since many callers aren’t aware of this, they stay on the line for longer.
Toll Fraud
Toll fraud happens when hackers break into a VoIP network in order to sell long distance minutes. The compromised PBX system is then used to complete the calls.
Carolina Digital Phone: Keeping Our Customers Safe from VoIP Fraud
While VoIP fraud is a significant problem, Carolina Digital Phone customers are protected through our comprehensive 24/7/365 Telecommunications Fraud Management System that:
- Monitors all outbound traffic to detect anomalies at the automatic number identification (ANI) level.
- Automatically blocks suspicious calling that may be the result of subscription fraud, IP PBX hacking, abuse of service terms and conditions, internal fraud, employee theft, phishing, pharming, and payment fraud.
- Uses customized system rules using conditional criteria, which are based on known fraud trends and tactics.
- Flags calls to/from numbers linked to confirmed fraud cases noted on industry-wide “hot lists”.
- Builds and scores profiles based on key risk indicators, such as volume, dialed destination, etc.
- Analyzes robocalls by researching and analyzing each telephone number, and accessing carrier and consumer reports.
- Automatically notifies customers if fraudulent activity is suspected or detected.
Enhanced Security and Encryption
 In addition, our hosted VoIP phone system is NOT run on the public internet. It is managed on a private and highly secure data network, which is protected by end-to-end encryption mechanisms including Transport Layer Security/TLS and Secure RTP for transmitting media, and robust password protection for managed routers and secure web-based dashboard access. Plus, our expert team installs and configures all security patches and updates.
In addition, our hosted VoIP phone system is NOT run on the public internet. It is managed on a private and highly secure data network, which is protected by end-to-end encryption mechanisms including Transport Layer Security/TLS and Secure RTP for transmitting media, and robust password protection for managed routers and secure web-based dashboard access. Plus, our expert team installs and configures all security patches and updates.
Working to Combat Robocalls
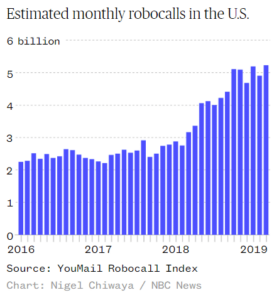 Robocalls have skyrocketed in recent years, with the call-blocking service YouMail estimating that 5.2 billion calls were placed to U.S. numbers in March, up from 2.5 billion three years earlier. National carriers are in the early stages of implementing new protocols aimed at stamping out one of the most common tactics used by robocall scammers. Inteliquent, our primary inbound origination carrier, is a member of both the CTIA Robocall Working Group and the US Telecom traceback group. We utilize Inteliquent’s internal fraud monitoring technologies and tools to track down illegal and abusive calling patterns, and we work directly with our customers to identify and control this traffic. Where permitted by laws and regulations, we also deploy call control capabilities to block/modify the flow of calls that have been identified as part of an illegal pattern. Furthermore, the CNAM DIP service on our TNs includes Neustar’s Robocall identification service, which identifies possible robocalls and allows end users to decide whether or not to answer the call.
Robocalls have skyrocketed in recent years, with the call-blocking service YouMail estimating that 5.2 billion calls were placed to U.S. numbers in March, up from 2.5 billion three years earlier. National carriers are in the early stages of implementing new protocols aimed at stamping out one of the most common tactics used by robocall scammers. Inteliquent, our primary inbound origination carrier, is a member of both the CTIA Robocall Working Group and the US Telecom traceback group. We utilize Inteliquent’s internal fraud monitoring technologies and tools to track down illegal and abusive calling patterns, and we work directly with our customers to identify and control this traffic. Where permitted by laws and regulations, we also deploy call control capabilities to block/modify the flow of calls that have been identified as part of an illegal pattern. Furthermore, the CNAM DIP service on our TNs includes Neustar’s Robocall identification service, which identifies possible robocalls and allows end users to decide whether or not to answer the call.
When rolled out across major networks, the telephone industry hopes that STIR/SHAKEN will eliminate neighbor spoofing, where scammers trick a caller ID into believing that a call is coming from the recipient’s area code. If a call has been verified, the number on the caller ID is definitely the number the call came from. Industry experts say getting rid of spoofing’s biggest benefit will be that it allows call-blocking services to more accurately flag scam calls.
STIR/SHAKEN
 STIR (Secure Telephone Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using toKENs) uses digital certificates, based on common public key cryptography techniques, to ensure that the calling number of a phone call is secure. Each telephone service provider obtains their digital certificate from a single trusted industry certificate authority, and the certificate technology enables “call traceability” back to the call source, which service providers can use to evaluate and identify calls as legitimate or illegitimate.
STIR (Secure Telephone Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using toKENs) uses digital certificates, based on common public key cryptography techniques, to ensure that the calling number of a phone call is secure. Each telephone service provider obtains their digital certificate from a single trusted industry certificate authority, and the certificate technology enables “call traceability” back to the call source, which service providers can use to evaluate and identify calls as legitimate or illegitimate.
This change is coming in part because the FCC has demanded it. In November 2018, FCC Chairman Ajit Pai said in a statement that he “demanded that the phone industry adopt a robust call authentication system to combat illegal caller ID spoofing and launch that system no later than next year.” It was a rare act of regulatory insistence from an enforcement-adverse leader best known for his dismantling of Obama-era Net Neutrality protections.
We are actively engaged with industry groups and other carriers to drive change and lead STIR/SHAKEN implementation practices. We plan on issuing an update towards the end of 2019.
To learn more about how we keep our customers safe from VoIP fraud and other types of system misuse, contact us today at (336) 544-4000 for your free, no risk, and no obligation consultation. We can visit your location, or connect with you over the web.

